What Exactly is Wireless Security?
Wireless security is the prevention of unauthorised users from accessing and stealing data from your wireless network. To put it another way, wireless security protects against unwanted access to a Wi-Fi network.
In our internet-obsessed day, wireless security, which includes encryption mechanisms and other security measures to preserve data carried over Wi-Fi networks, is critical.
Wi-Fi has created new chances for criminals, and Wi-Fi security is one of the most important preventive steps to help reduce cybercrime.
Now that we’ve introduced the concept of wireless security let’s look at ‘what is a wireless network?’
What Exactly Is a Wireless Network, Also Known as Wi-Fi?
Residential, commercial, and telecommunications networks all use wireless networks. In essence, a wireless network is a computer network that connects network nodes via Radio Frequency (RF) communication.
People frequently ask, “What is a wireless network?” Because, despite the fact that they are almost wherever people work and live, their operation is frequently a mystery. Similarly, many people mistake all wireless for Wi-Fi and are astonished to learn that the two are not the same.
Yes, both use radio frequency (RF). Despite the fact that both use RF, many different types of wireless networks use different technology (Bluetooth, ZigBee, LTE, 5G). Wi-Fi, on the other hand, is a wireless technology defined by the Institute of Electrical and Electronics Engineers (IEEE) in the 802.11 specification and subsequent upgrades.
Now that we’ve covered the principles of networking, let’s take a look at the many forms of wireless network connections.
Wireless Network Connection Types – Wireless Security
Local Area Network (LAN)
A local-area network (LAN) is a computer network that is restricted to a certain location, such as an office building. It is capable of connecting a wide range of components, including computers, printers, and data storage devices.
To connect everything in a LAN, switches, access points, routers, firewalls, and ethernet cables are used. The most well-known wireless LAN is Wi-Fi.
Personal Area Network (PAN)
A personal-area network (PAN) is a network that is focused on one person’s devices in one location. Computers, phones, video game consoles, and other peripheral devices may be found in a PAN. They are widespread in single-family homes and small office buildings. Bluetooth is the most widely used wireless PAN.
Metro Area Network (MAN) (MAN)
A metropolitan-area network (MAN) is a computer network that connects a city, a geographical region, a corporate or a college campus, or both. The size of a MAN distinguishes it from a LAN. Depending on the needs of the business, a MAN may encompass many square kilometres. A LAN is often comprised of a single building or region.
Big organisations, for example, may hire a MAN if they have a large campus and need critical components such as heating, ventilation, and electrical systems.
Wide Area Network (WAN) (WAN)
A wide-area network serves a broad geographic area, such as an entire city, state, or country. In reality, the internet is a wide area network (WAN). A WAN, like the internet, can be composed of smaller networks such as LANs or MANs. The most well-known wireless WANs are cellular services.
In today’s corporate environment, these various types of wireless networking are critical for keeping employees connected to the internet. Wi-Fi, on the other hand, is extremely vulnerable to hackers. This is where the requirement for strong wireless security, as provided by wireless security protocols, comes into play.
Protocols for Wireless Network Security
Wireless networks are becoming more widespread in both commercial and residential settings. The wireless network connected with the device’s brand or carrier is currently available on the majority of mobile devices. Public WiFi allows you to catch up on work or interact with pals online. Public hotspots may be available in restaurants, coffee shops, and airports, to mention a few.
The primary problem with wireless networks is their lack of security. However, there are measures you can take to boost WiFi security and secure your data from hackers and thieves.
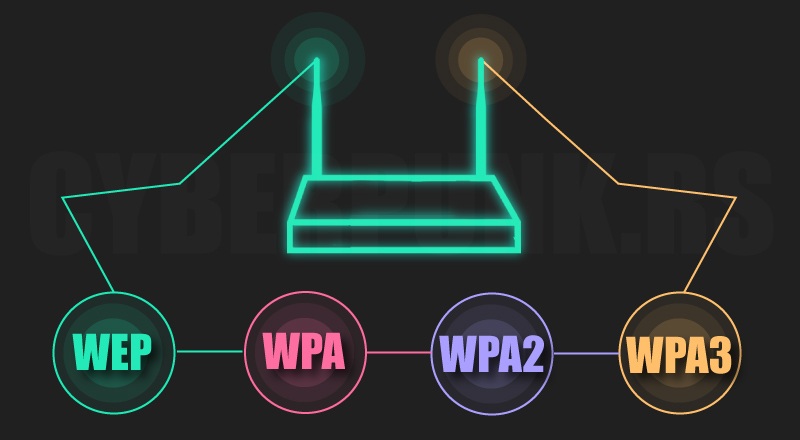
There are four types of wireless security protocols. Each protocol serves a certain purpose and has a varying level of strength. The Wi-Fi Alliance, which promotes wireless technology and interoperability, created these standards.
WEP is an abbreviation for World Wide (Wired Equivalent Privacy)
WEP, which was designed for wireless networks, was adopted as a Wi-Fi security standard in September 1999. WEP has a number of well-known security flaws, is easy to crack, and is difficult to configure.
Because WEP is not the best option for network security, various wireless security alternatives have been developed. The Wi-Fi Alliance formally abandoned WEP in 2004.
WPA (Wi-Fi Protected Access)
In 2003, WPA (Wi-Fi Protected Access) was created. It was created as a result of weaknesses discovered in the WEP protocol. WPA was created to temporarily supplement the security of WEP.
Wi-Fi Protected Access (WPA) employs the Temporal Key Integrity Protocol (TKIP), which dynamically changes the system’s key to provide stronger (128/256-bit) encryption than WEP. TKIP prohibits hackers from creating an encryption key that is comparable to that of the secure network.
WPA was a substantial improvement over WEP, but because the primary components were intended to be distributed through firmware upgrades on WEP-enabled devices, they still relied on compromised elements and were subject to infiltration.
WPA2 stands for Wi-Fi Protected Access (Wi-Fi Protected Access 2)
The current default algorithm is WPA2, often known as WPA2-Personal.
The WPA2 protocol was initially introduced in 2004. The use of AES in WPA2 was the most significant improvement over WPA (Advanced Encryption Standard).
The US government recognises AES for encrypting sensitive data. As a result, it is sufficient for protecting residential networks.
At the time, the most important vulnerability of a WPA2 system is when an attacker gets prior access to a secured Wi-Fi network and obtains specific keys to launch an attack on other devices on the network.
Security recommendations for known WPA2 vulnerabilities apply mostly to enterprise-level networks and are insignificant for smaller home networks.
WPA3 (Wi-Fi Protected Access 3)
WPA3 represents the first significant development in wireless security in 14 years.
One of the most important aspects of cybersecurity is protecting Wi-Fi from cybercriminals. As a result, you should pay attention to the release of WPA3, the next-generation wireless security standard: It will make Wi-Fi connections more secure and keep you safe from security threats.
Begin by considering how WPA3 will safeguard you at home. It will expressly limit the damage caused by your careless passwords.
WPA2 has a fatal flaw in that it allows hackers to guess your password via an offline dictionary attack. Without being on the same network, an attacker can guess your credentials as many times as they want, fast cycling through the entire dictionary.
WPA3 will defend against dictionary attacks with a new key exchange method.
If your password is still compromised, you will receive an additional reward. WPA3 now enables forward secrecy, which means that any communication that passes through your transom before an unauthorised party gains access is encrypted. They can even interpret out-of-date WPA2 traffic.
WPA3 is backwards compatible with WPA2 devices to encourage more effective implementation. It should be noted, however, that the WP3 protocol can only be used with routers manufactured in 2019 or after.
Let’s take a look at the hazards to your wireless network as we proceed through the world of wireless security.
What are the Security Risks to Your Wireless Network?
The dangers of an unprotected wireless network are the same whether it is a home network or a business network. Among the dangers are:
Password Decryption and Cracking
Password cracking and decryption is a time-honored method that involves a “brute force assault.” This attack is based on trial and error, with the hope of finally getting it right. Hackers, on the other hand, can use a range of tools to speed up the process.
Piggybacking
If your wireless network is open to the public, anyone with a wireless-enabled computer within range of your access point can connect to it.
The typical interior broadcast range of an access point is 150–300 feet. It has a range of up to 1,000 feet in the open air.
As a result, whether you live in a densely populated area or in an apartment or condominium, failing to secure your wireless network may expose your internet connection to a large number of unauthorised users. These users may conduct illegal actions, collect and monitor your web traffic, or steal personal information.
Wardriving
Wardriving is a type of piggybacking.
The broadcast range of a wireless access point can make internet connections available outside your home, even as far as your street.
Astute computer users are aware of the concept of access range. Some people make a pastime of driving about cities and neighbourhoods with a wifi-enabled computer, generally outfitted with a huge antenna, in search of unprotected wireless networks.
The term “wardriving” refers to this piggyback version.
The Evil Twin Assaults
An attacker uses an evil twin technique to collect information about a public network access point and then configures their computer to look like it.
Unwary users connect to the stronger signal because the attacker’s broadcast signal is stronger than the authorised access point’s.
Because the victim connects to the internet through the attacker’s system, the attacker has easy access to any data exchanged over the internet using specialised tools.
Credit card numbers, login and password combinations, and other sensitive information may be included in this data.
Before using a public Wi-Fi hotspot, always double-check the name and password. This ensures that you are connected to a reliable access point.
Sniffing Wireless
Many public access points are unsafe, and the data they transmit is unencrypted. If meaningful conversations or transactions are not encrypted, they may be jeopardised.
Because your connection is broadcast “in the clear,” bad actors using sniffing tools may be able to collect sensitive information like credit card numbers and passwords.
To strengthen wireless security, make sure that all of the access points you connect employ WPA2 encryption at the very least.
Computer Unauthorized Access
An unsecured public wifi network and unsecured file-sharing may enable a hostile individual to review any folders and files you have mistakenly shared.
When connecting your devices to public networks, turn off file and folder sharing. Allow sharing only on authorised home networks and when data exchange is truly necessary.
When not in use, make sure to turn off file sharing. Turning it off will help prevent an unknown attacker from gaining access to your device’s data and jeopardising your wireless security.
Surfing on the Shoulders
While typing in public places, malicious actors can spy on you. Simply watching you, they can steal important or confidential information.
Screen guards are inexpensive and prevent shoulder-surfers from reaching your device’s screen. Be careful of your surroundings when accessing sensitive information or entering passwords on small devices such as phones.
Attacks by a Man-in-the-Middle
A man-in-the-middle (MITM) cyber assault is a potentially dangerous sort of cyber attack. By imitating a rogue access point and collecting login credentials, a hacker gains access to a private network.
The attacker instals hardware that masquerades as a trusted network, such as Wi-Fi, in order to mislead unsuspecting victims into connecting to it and handing over their credentials.
MITM attacks can occur anywhere because devices will join to the network using the strongest signal and whatever SSID name they can recall.
Now that we’ve covered the potential risks to your wireless network, let’s have a look at how to wirelessly secure your home Wi-Fi network.
How Do I Safeguard My Home Wi-Fi?
Almost every member of the household has access to it through laptops, PCs, cell phones, and tablets.
Criminals can acquire access to virtually all Wi-Fi devices by exploiting a minor flaw in your home Wi-Fi network. Access could cause issues with bank accounts, credit card information, child safety, and a variety of other issues.
The following suggestions may assist you in protecting your home Wi-Fi network from illegal access.
1. Modify the name of your home Wi-Fi network.
The first step in configuring your home network’s wireless security is to alter the SSID (service set identifier). The SSID of a network identifies it.
Many manufacturers assign a default SSID to all of their wireless routers. Most of the time, it is the name of the company.
The SSID is used to identify each publicly broadcast network when a computer with a wireless connection searches for and shows nearby wireless networks.

This raises the chances of a hacker breaking into your network.
Change the network’s SSID to something that does not expose any personal information to prevent hackers from jeopardising your wireless security.
2. Change the passwords that are set by default.
To make configuration easier, the bulk of network equipment, including wireless access points, comes with pre-configured default administrator passwords.
Because default passwords are easily obtained online, they only give a limited level of security.
Increasing the difficulty of guessing default passwords makes it more difficult for attackers to get access to a device. Using and changing complicated passwords on a regular basis is your first line of defence in protecting your device.
3. Make use of the latest recent WPA network encryption.
As we described in the last section, there are numerous types of Wi-Fi security that you can use for your home Wi-Fi. Make it a point to always use the most recent version that is available.
If your router only provides Wired Equivalent Privacy (WEP) protection, it should be replaced because it is most certainly out of date in other respects.
WPA is adequate; WPA2 is significantly superior and is most likely the most recent version that most routers today can support, and it is adequate. WPA3 is the most recent version available, but not all routers support it; if possible, make the switch to increase your wireless security.
You may alter your Wi-Fi encryption in the router’s settings, which is also where you can change your password.
4. Make sure your router is up to date.
Before installing a new router or upgrading an old one, check the manufacturer’s website to see whether a more recent version of the software is available for download.
To ensure you obtain the most recent version, register your router with the manufacturer and sign up for updates. If you purchased your router through an Internet Service Provider (ISP) like Verizon or Comcast, check with them to see if they offer automatic upgrades.
5. Create a guest network.
Many routers allow you to create a guest network with its own name and password. It’s a sensible security precaution for two reasons:
1. Having a secondary login ensures that only a few people know your primary Wi-Fi network password.
2. If a guest accidentally has spyware on their phone or tablet, it will not get onto your main network or your devices.
6. Ensure that you have a solid firewall in place.
A “firewall” is a software application that protects computers against malicious invasions.
Wireless routers typically include built-in firewalls; nonetheless, the firewall is deactivated on occasion. Check that the wireless router’s firewall is enabled.
If your router does not have a firewall, make sure you install a reliable firewall solution on your system to check for unauthorised access and boost your wireless security.
7. It is essential to have commercial-grade antivirus software.
Install and keep your virus definitions up to date with commercial-grade antivirus software. Spyware and adware detection and protection technologies are now included in commercial-grade antivirus software.
I Use and Recommend Commercial-Grade Antivirus Software
Sophos Home Premium, developed by Sophos Limited, a British company specialising in digital security, is my go-to antivirus software.
The security company specialises in award-winning security and privacy solutions, next-generation protection, mobile security and management, and network, server, and endpoint protection for consumers and organisations alike.
To keep track of application activity on your home computer network, Sophos Home Premium leverages the same advanced artificial intelligence used in commercial antivirus security solutions for large corporations experiencing ongoing ransomware assaults.
It looks to see if any of the software applications on your machine have any unusual ransomware features.
Sophos Home Premium can detect and eradicate previously unknown and undetected ransomware.
Sophos now protects home computers at the same level as it does over 300 million business devices worldwide.
Visit this page to learn more about Sopho’s commercial-grade antivirus protection for your home.
This post: Wireless Security – From A to Z – Types, Threats, To How to Secure first appeared on https://websecurityhome.com/
Brought To You By:
The post Wireless Security – From A to Z – Types, Threats, To How to Secure appeared first on https://cable13.com
The post Wireless Security – From A to Z – Types, Threats, To How to Secure appeared first on https://gqcentral.co.uk








Comments are closed